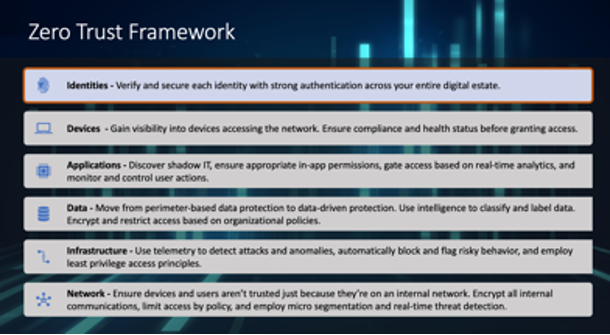
As COVID forced organizations around the world to send their workforce home, creating the work from home (WFH) phenomenon, IT and security teams rapidly focused on Zero Trust approaches to security to mitigate challenges of enabling secure remote work. Modern workplace employees are getting their work done any way they can these days – using personal devices, sharing data through new services, maxing out home WiFi, and collaborating outside the confines of traditional corporate network security. It has created an IT balancing act between security and WFH productivity.
Read MoreKen Bergeron
Recent Posts
Secure access to email and other business productivity tools continues to be a top priority for IT administrators. Microsoft services, such as Azure Active Directory and Office 365, use OpenID Connect for authentication and OAuth 2.0 for authorization. Here’s how that process works: When Outlook connects to Exchange Online, the API requests are authorized using OAuth 2.0 Access Tokens. They are valid for one hour. When the tokens expire, the Outlook client is redirected back to Azure AD to refresh them. This provides an opportunity to re-evaluate policies for user access. If a user has been disabled in the directory or because of a Conditional Access policy, the admin might choose not to refresh the token.
Read MoreSubscribe to the Daymark Blog
Latest Posts
Browse by Tag
- Cloud (68)
- Security (42)
- Microsoft (38)
- Azure (35)
- Partners (32)
- Data Protection (29)
- Data Center (26)
- Backup (24)
- Daymark News (23)
- Compliance (20)
- Data Governance (18)
- Veritas (18)
- Virtualization (18)
- Storage (17)
- CMMC (13)
- Cloud Backup (13)
- Cybersecurity (13)
- Disaster Recovery (13)
- Managed Services (13)
- Government Cloud (10)
- Featured Gov (9)
- Industry Expertise (9)
- GCC High (7)
- Networking (6)
- AI (5)
- Hybrid Cloud (5)
- NIST SP 800-171 (3)
- Reporting (3)
- Copilot for Microsoft 365 (2)
- GDPR (2)
- Services (2)
- Cloud Security (1)
- Mobile (1)
- Reporting-as-a-Service (1)