
Cybercriminals continue to use phishing attacks on individuals within enterprises. With increased sophistication and multiple attack vectors, businesses must be vigilant at every step of the way to prevent infiltration. Let me share a recent example-
Today I received an email from a recruiter. It’s not out of the ordinary for recruiters to ping us with resumes hoping that we will see a fit for their candidate. This one was well written, had a company logo, and a picture of the sender. Including pictures is a growing trend with recruiters
This recruiter found a posting on our website for a senior networking position and attached a PDF of a resume. So far, this all seems like a pretty standard business interaction, right? The attachment made it through Mimecast – our email security management solution. Getting through Mimecast tells me it was sandboxed first. This means that Mimecast used a one time instance of all the flavors of Windows, Mac, and Linux to try and open the attachment and see if it did anything malicious. Since it did not, it made it through to my inbox.
I didn’t see this at first but I assumed they sent a clean document so it would get through a filter. There is nothing out of the ordinary about the resume. It appears that it was used as a validation and so again this email still looks legit.
The signature field from the sender had some fairly standard, probably mandatory, text – again seems real. A lot of phishing attempts have some sort of flaw in the content. Badly written sentences, typos, missing signature, no logo, incorrect punctuation, etc. This one did not have anything that stood out as concerning.
Of course I want to click on the links to see who this person is and what is on the LinkedIn profile. If I were actually looking for a networking candidate this seems like the next logical step to validate this person and her company.
But at last the truth is discovered. Clicking on the link would have led me to something dangerous, potentially catastrophic. When I clicked the link, Mimecast was there to check what was at the end of the link -- and what it told me was that as valid as this email looked, it was far from a legitimate recruiter looking to place a candidate at our company.
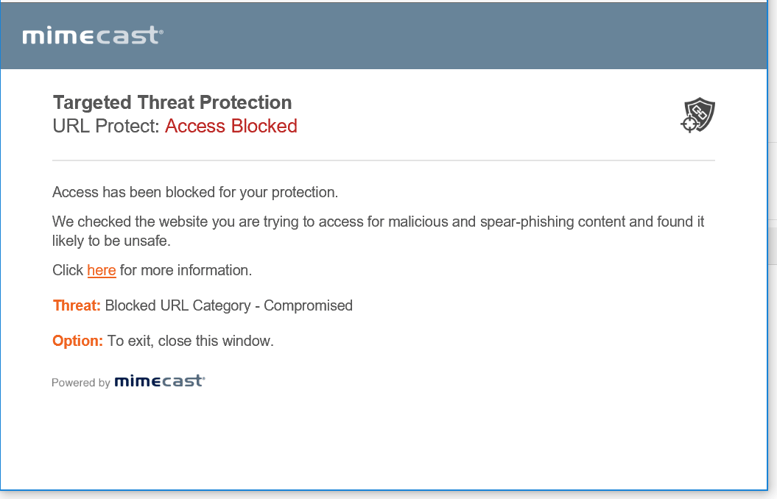
The link could have been a malware executable, or a landing page with malicious code in it, or something even worse. Thankfully, I will never know.
Strong security can be painful at times, but I assure you whatever was on the other side of that link was much worse. Oh, and I still have a fully functioning laptop, the data on my laptop is safe, and I won’t unknowingly compromise the rest of the company when I plug into the network tomorrow morning!



