Impossible travel. Is it sending a human to Saturn or Venus? Well maybe, but in the context of Microsoft Office 365, Impossible Travel is a security feature that is a great indicator of potential hacking attempts. The concept is straightforward. If you login to Office 365 from your office in Boston and then 20 minutes later you try to login from Dallas, or you login from home in Chicago and five hours later from Beijing, Office 365 basically says “wait a minute, that’s impossible” and it denies login from Dallas and immediately sends an IT security alert. Get tips to optimize Impossible Travel here.
Read MoreMicrosoft’s Ignite Conference was back to a face-to-face event his year in Seattle, Washington. The Daymark Solutions team was there soaking up the latest Microsoft has to offer and absorbing what’s in the works for the year ahead. This year’s conference theme of “doing more with less” spoke to the immense value of Microsoft’s product portfolio. From Power Platform’s low-code/no-code improvements to a host of new solutions under the Microsoft Entra, Purview and Viva umbrellas, doing more with less is really about making our lives easier in the modern digital work era we live in while providing first-in-class technology and security. The following are some notable takeaways from this year’s Ignite.
Microsoft Intune Premium - Advanced Management Suite
- What’s the Scoop?
Microsoft recently held its annual Ignite Conference where they announced over 100 updates to its suite of cloud services and products. Daymark was on the ground at the Convention Center in Seattle to explore the innovations and engage with Microsoft on the latest changes. 100 updates is a lot to digest! Here are our thoughts on 5 important ones worth paying attention to.
1. Microsoft Teams Premium
What is it?
Microsoft Teams Premium is an add-on scheduled for release in December of this year, and will provide exciting new features around security, artificial intelligence, and personalization
Why is it important?
The AI will provide intelligent meeting summaries and will automatically assign tasks based on its review/recap of the meeting. In addition, it will provide personalized insights in meeting recordings that will call out important moments in the meeting, such as when a user’s name was mentioned, a screen was shared and when people have joined or left.
Read MoreMicrosoft’s Azure Government has become a trusted cloud for US government agencies, contractors and the Defense Industrial Based (DIB), providing unified security to protect the nation's data, and solutions for secure remote collaboration. Microsoft’s Azure Government uses the same underlying technologies as Azure, which includes the core components of Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), and Software-as-a-Service (SaaS). The increased security is achieved because it is a physically isolated sovereign cloud environment dedicated to US federal, state, local, and tribal governments, and their partners. It provides an extra layer of protection to mission-critical workloads through contractual commitments regarding storage of customer data that is subject to various US government regulations such as Export Administration Regulations (EAR) and International Traffic in Arms (ITAR). Azure Government offers additional security by relying on screened US personnel.
Azure Government and CMMC
Read MoreMicrosoft 365 GCC vs. GCC High
How do you know which level of GCC is right for you? Here’s key criteria to help you distinguish GCC and GCC High so that your organization makes the move to the right cloud.
Government Community Cloud (GCC)
You can think of GCC as a government version of the Microsoft 365 commercial environment. It resides on the Azure Commercial infrastructure and has many of the same features, but servers must be located in the continental United States (CONUS) as mandated by FedRAMP Moderate. Although the servers are only in CONUS, access to data is available on a global basis. In general, non-defense-related government agencies and contractors can deploy GCC.
Read MoreCloud security is a constant concern for organizations of every size. Stopping malicious actors from accessing your company’s systems and data is a top priority, but is made difficult by the number of different exploit techniques coupled with the sophistication of the attacks. One area of particular concern is legitimately compromised user credentials. For example, if a password I use frequently (maybe even a strong one) is exposed in a breach of an e-commerce company. The malicious actor located in Moscow who obtains this userID (likely an email of mine) and password then does a quick lookup on LinkedIn and finds that I work at Daymark. From here, the exploit is obvious. They now have a legitimate username and password combination and while we do employ multi-factor, there are constant threats to that.
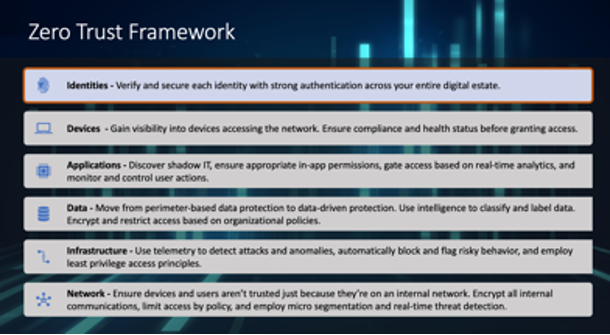
Read MoreAs COVID forced organizations around the world to send their workforce home, creating the work from home (WFH) phenomenon, IT and security teams rapidly focused on Zero Trust approaches to security to mitigate challenges of enabling secure remote work. Modern workplace employees are getting their work done any way they can these days – using personal devices, sharing data through new services, maxing out home WiFi, and collaborating outside the confines of traditional corporate network security. It has created an IT balancing act between security and WFH productivity.
Read MoreConditional Access in Azure AD provides a level of security required to maintain appropriate controls over who can access confidential and privileged information. It was the topic of discussion at our most recent “Ask the Engineer Q&A Roundtable” where attendees learned tips for a successful Conditional Access deployment and got answers to their specific questions.
Read MoreIt’s a crazy time out there. Businesses have been mandated by state governments to enable employees to work from home. Literally overnight, there have been massive shifts to connect people remotely. Suddenly even your grandparents know what Zoom is!
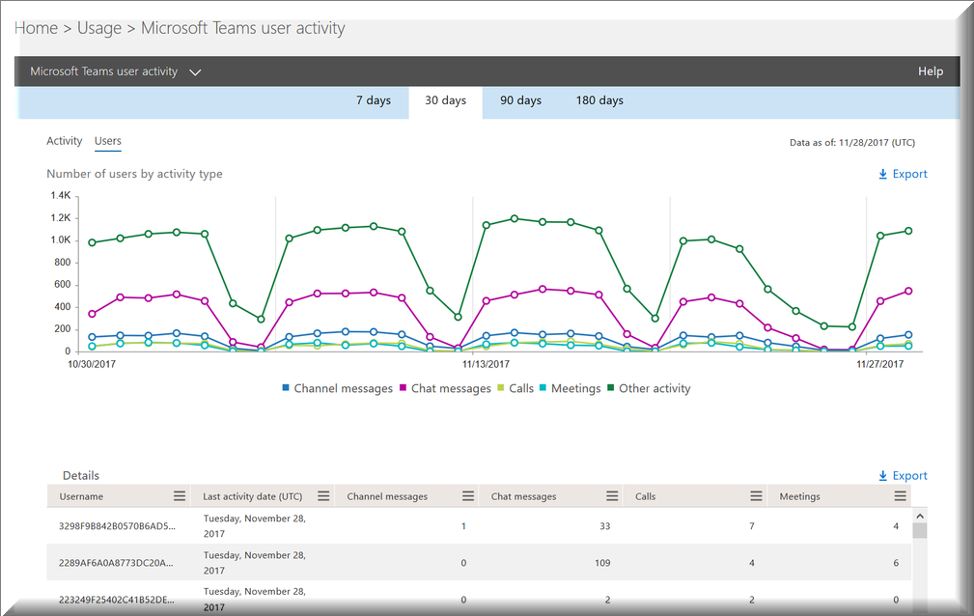
Microsoft Teams is playing an integral part in facilitating remote communication and collaboration. Most companies with Office 365 subscriptions already have licenses for this product, but just now are really rushed to enable Teams for the massive increase of remote workers.
Read MoreOn February 11 2020, Microsoft released a patch for Exchange Servers that would fix a vulnerability pertaining to unauthorized access to the backend of the Exchange Control Panel. There is now confirmation from a source at the United States Department of Defense that multiple nation-state backed actors and other ransomware gangs are actively and maliciously exploiting this vulnerability on unpatched systems. The vulnerability results from the Exchange Server failing to properly create unique cryptographic keys at the time of installation. The hackers’ sophisticated exploits circumvent encryption, granting them full access of the server.
It is imperative that the latest patches from February 11th be applied as even a single Exchange instance puts you at risk.
Read MoreSubscribe to the Daymark Blog
Latest Posts
Browse by Tag
- Cloud (68)
- Security (42)
- Microsoft (38)
- Azure (35)
- Partners (32)
- Data Protection (29)
- Data Center (26)
- Backup (24)
- Daymark News (23)
- Compliance (20)
- Data Governance (18)
- Veritas (18)
- Virtualization (18)
- Storage (17)
- CMMC (13)
- Cloud Backup (13)
- Cybersecurity (13)
- Disaster Recovery (13)
- Managed Services (13)
- Government Cloud (10)
- Featured Gov (9)
- Industry Expertise (9)
- GCC High (7)
- Networking (6)
- AI (5)
- Hybrid Cloud (5)
- NIST SP 800-171 (3)
- Reporting (3)
- Copilot for Microsoft 365 (2)
- GDPR (2)
- Services (2)
- Cloud Security (1)
- Mobile (1)
- Reporting-as-a-Service (1)