
Understanding the Cybersecurity Maturity Model Certification (CMMC)
Get started with cmmc complianceWhat DIB Contractors Need to Know
The Cybersecurity Maturity Model Certification (CMMC) is the DoD program to dynamically enhance DIB cybersecurity and protect against compromise of sensitive defense information on contractors’ systems and acts as a unified standard for implementing cybersecurity across the defense industrial base.
The CMMC Framework is used by the government to certify and verify exactly how safe you are to conduct business. CMMC is intended to standardize and raise the bar for cybersecurity among DIB contractors. It uses CMMC third-party assessment organizations of contractors’ compliance with certain mandatory practices, procedures and capabilities that can adapt to evolving cyber threats. In November 2021, the DoD announced CMMC 2.13. Learn about key changes and timelines associated with CMMC 2.13.
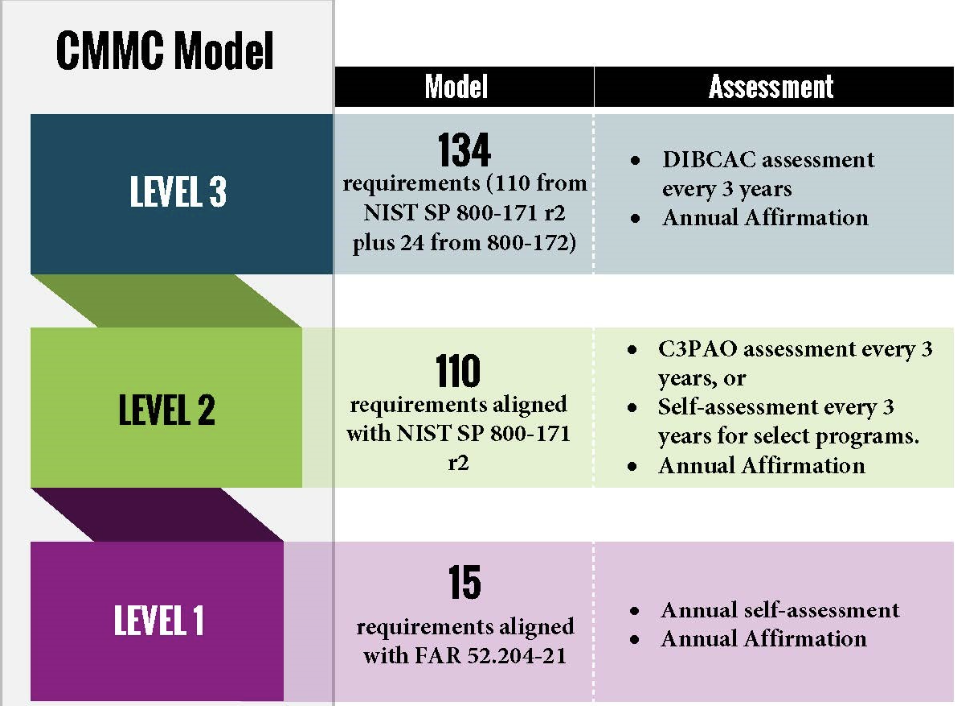
CMMC 1.0 had five certification levels (CMMC 2.13 has three) that reflect the maturity and reliability of a company’s cybersecurity infrastructure to safeguard sensitive government information. The five levels are tiered and build upon each other’s technical requirements. Get the cybersecurity agility you need in order to properly handle government data.
KEY FEATURES OF CMMC 2.0
PREPARE FOR CMMC READINESS
We enable DIB contractors to meet strict government and regulatory compliance requirements related to CMMC controls for FCI and CUI (ITAR, CDI and CTI) data. Learn how we can help you prepare for CMMC readiness.
GCC High and Azure Government for
CMMC Compliance
GCC, GCC High and Azure Government support government contractors, as well as the federal government, to meet the terms of cybersecurity and compliance. Even though GCC High is not a primary requirement of CMMC it is highly recommended. If you need to be certified in CMMC Level 3 (CMMC 2.13 Level 2) and are handling existing Controlled Unclassified Information (CUI) and ITAR data in your cloud environment on a Microsoft Platform, you should move to GCC High.
Featured GCC High, Azure Government and CMMC Compliance Articles

CMMC 2.13 is Here - Explore the 2025 Timeline
On October 15, 2024, the final rule for the Cybersecurity Maturity Model Certification (CMMC) program was officially published. ...

What Government Subcontractors Should Know About DFARS Flowdowns
Protecting sensitive and classified information when working for the Federal Government requires constant vigilance. When the ...

How Much Will CMMC 2.0 Compliance Really Cost?
Many companies are currently evaluating how they might fund initiatives necessary to move their businesses towards compliance ...


